This Blog explain how to send log data from O365 and AD Azure logs to splunk. The log data includes Azure AD Audit and Login activity, Exchange Online, SharePoint, Teams, and OneDrive.
This Blog uses the Splunk Add-on for Microsoft Office 365 to collect log data from Azure AD and O365. Once that’s in place, the Microsoft 365 App for Splunk is used to visualize the log data.
The steps to send O365 log data to Splunk include:
- Add the Splunk Add-on for Microsoft Office 365
- Turn on Office 365 Audit Logging
- Create the Application in Azure AD
- Configure the Splunk Add-on for Microsoft Office 365
- Verify Logging
- Add the Microsoft 365 App for Splunk Add-on
Step 1: Login to splunk.
Step 2: Install splunk Add-on for Microsoft 365 – https://splunkbase.splunk.com/app/4055/
Step 3: Configure it
It will ask for tenant
Step 4: For that need to go portal.azure.com
Lets make sure the login is enabled
Step 5: Sign in to portal.office.com
Note: You need to be a global admin to perform the below steps.
Go to show all > security > Search > Audit log search
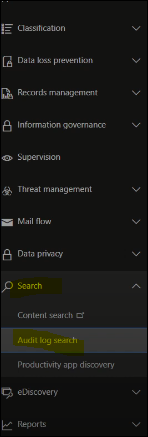
Step 6: Turn on auditing

NOTE: If you do not turn on auditing you won’t get the logs into splunk.

Step 7: Register and application.

Step 8: API permission -> Add permission.
Click on the Office 365 Management APIs box.

Step 9: Application permissions.
Expand and select each permission. This gives the App read permission to all the log files Splunk will collect. Click Add Permissions when finished.

Step10: Grant admin consent.
Log API Read Access
The permissions require admin consent to take effect. Click Grant Admin consent for “Tenant” to continue. Notice that some permissions have the status of not granted. These are duplicate, log collection will work with the permissions granted.

Step11: We will get the Client Id and Tenant Id.
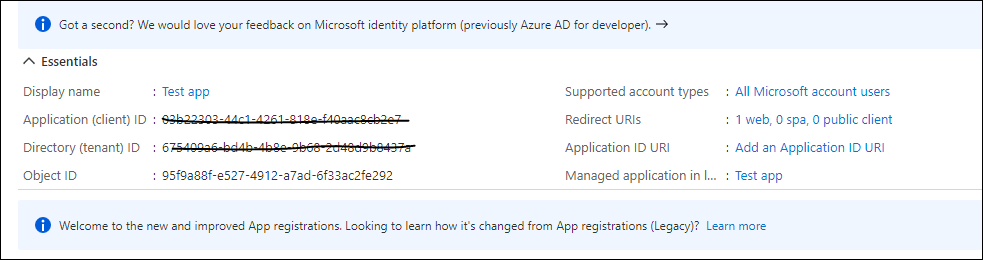
Step12: Add secret key
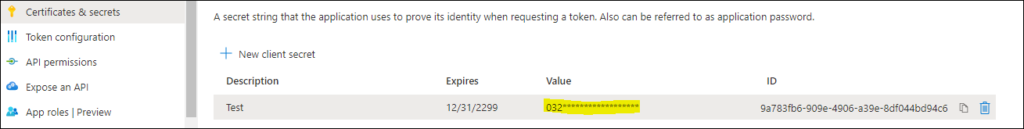
Configure the Splunk Add-on for Microsoft Office 365
Now that the App Registration is set up and we have the values needed, we can configure the Splunk Add-on for Microsoft Office 365.
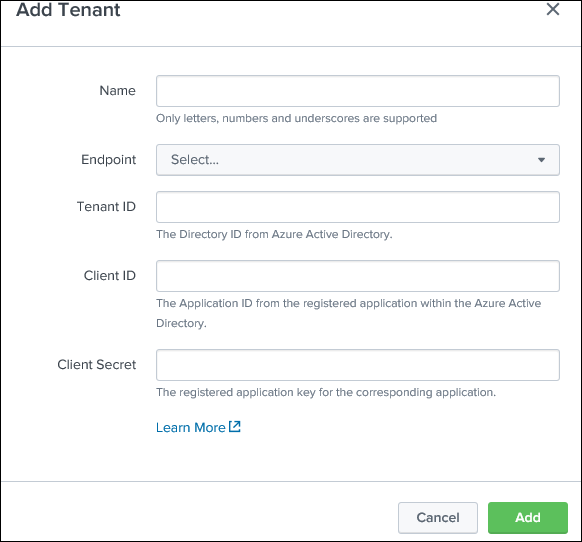
From Splunk, go to the Splunk Add-on for Microsoft Office 365, Tenant, and select Add Tenant.
Step 1: Add tenant

Step2: After tenant Add input

Verify logging
Log data will become available shortly after configuring the tenant and Inputs. Go to the Splunk home page and go to Search & Reporting .The two commands below should return Azure AD Data if log collection is set up correctly.
Step3: RUN this query.
Index=”main”
AND then
index="main" sourcetype="o365:management:activity" | search Operation!="UserLoggedIn" AND Operation!="TeamsSessionStarted"| table CreationTime,Operation,Workload
At this point, logging from Azure AD and O365 to Splunk is working. Log collection is not real-time. It can take 20 minutes or longer for data to show in the results.
Add the Microsoft 365 App for Splunk Add-on – https://splunkbase.splunk.com/app/3786/
Search and add the three add-ons to finish the Microsoft 365 app for Splunk install.
1. Sankey Diagram
2. Timeline
3. Semicircle Donut
Once finished, go to the Microsoft 365 App for Slunk from the Splunk home page. From here, navigate to find different visualizations of your organizational data.
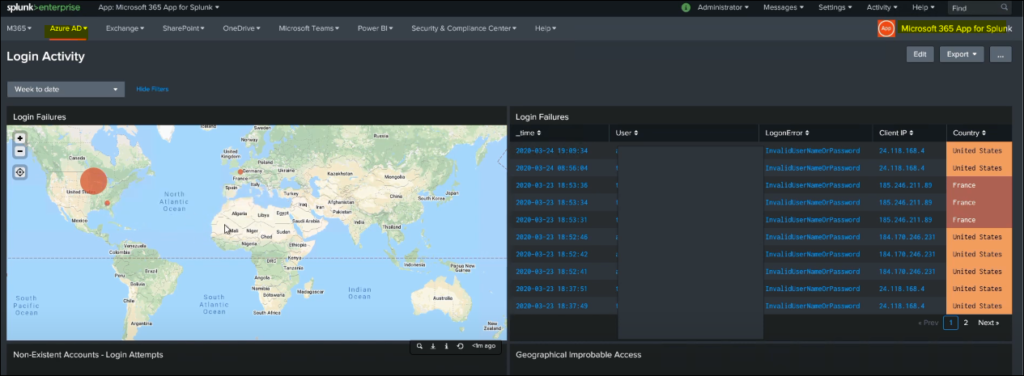
This allows us to pull the data logs from Microsoft 365 management API.
If you are still facing issue regarding azure logs to splunk topic Feel free to Ask Doubts in the Comment Box Below and Don’t Forget to Follow us on 👍 Social Networks, happy Splunking >😉