Today, we are going to discuss about Search Time Field Extraction in splunk. So, what is it exactly? The fields which we extract from our data which is already Indexed. Let us go through the procedure step by step.
Now, the initial step would be to write the Regular expression that will match and group the data that you need to extract. There are two ways using which we can extract the required fields.
Method 1:
Step 1: Go to Settings>Fields.
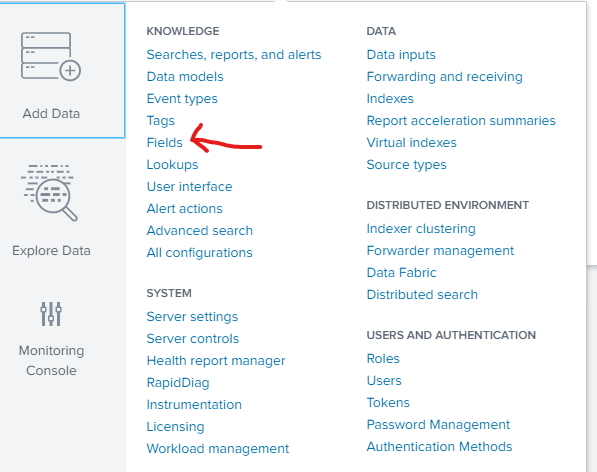
Step 2: click on Fields Extraction.
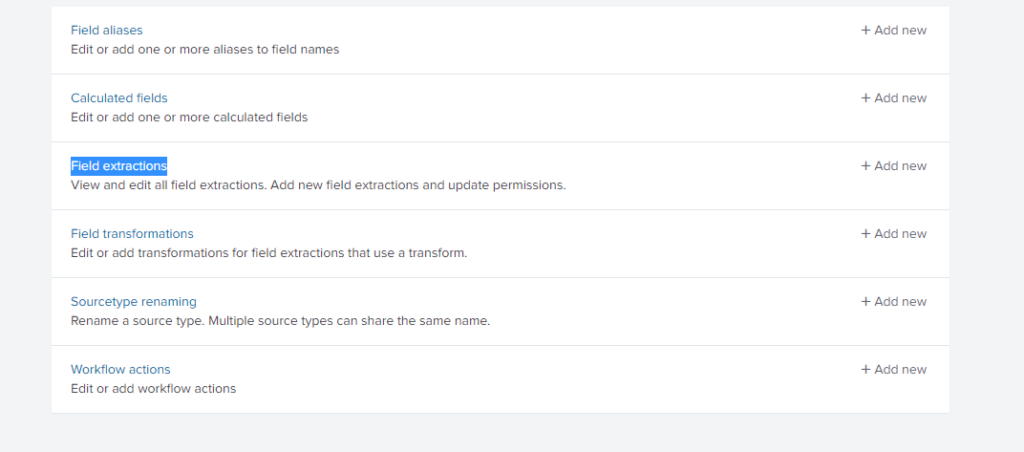
Step 3: click on New and fill in information regarding to the field you want to extract as shown below:
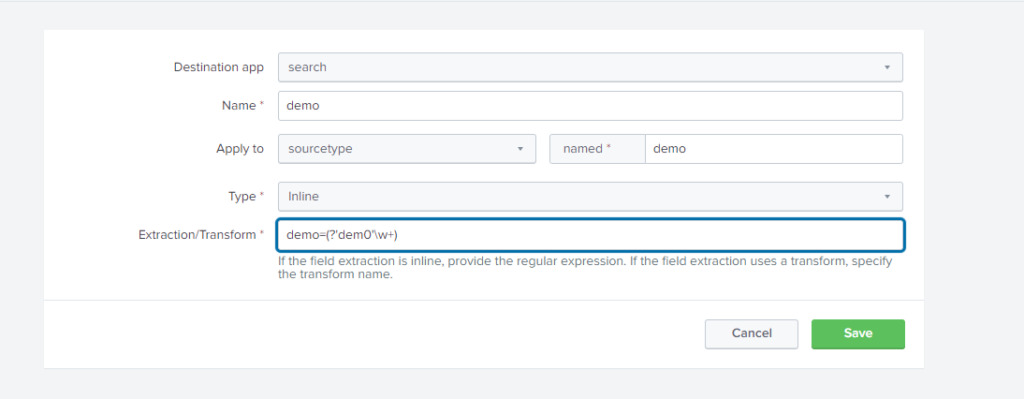
Here notice that we have selected Inline in Type. Enter the Regular expression that will match your data in Extraction/Transform and then click on save. After that change the permission of your extraction you just created to global by going to setting>Fields>Field Extraction
Now, let us look what happens at the backend in our Splunk. In order to do that Navigate to “$SPLUNK_HOME/etc/apps/search/local” and open the file named props.conf. A setting gets created as written below in our props.conf.
[demo]
EXTRACT-demo = demo=(?’demo’\w+)Method 2:
Step 1: Go to Setting>Fields> “Field transformations”, then click on add New.
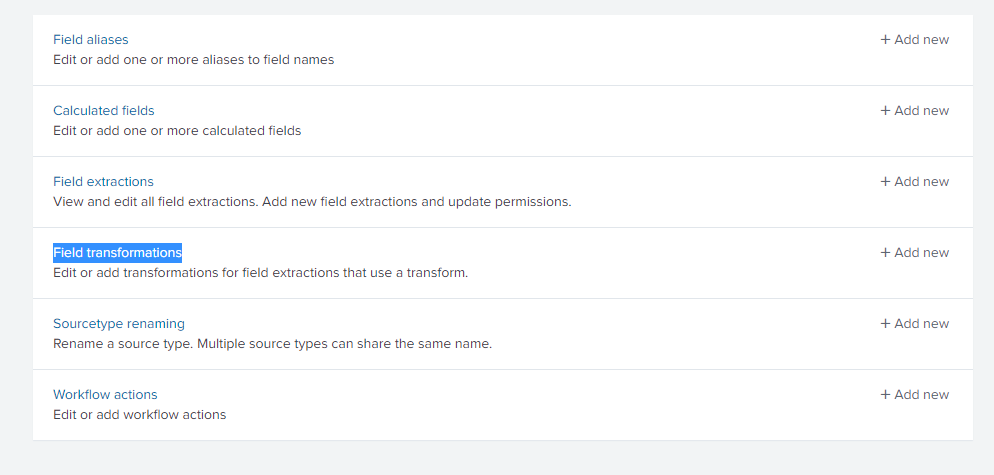
Step 2: Enter the required field as shown below:

In source Key we enter the field from which we want to extract. So, if you want to extract the data from a field already present then write that field name is source key.
Now if we navigate to “$SPLUNK_HOME/etc/apps/search/local”, this setting gets created in transforms.conf.

Now, we have to repeat the steps mentioned in Method-1.
Go to settings>fields>Field Extraction> click on new, and then write in the following way. And this time in Type select transform. And also, in Extraction/Transforms write the transform name you entered in Name while creating new fields transformations (in above fig. if you see, we have written server in Name that’s what we have to write in Extraction/Transform).
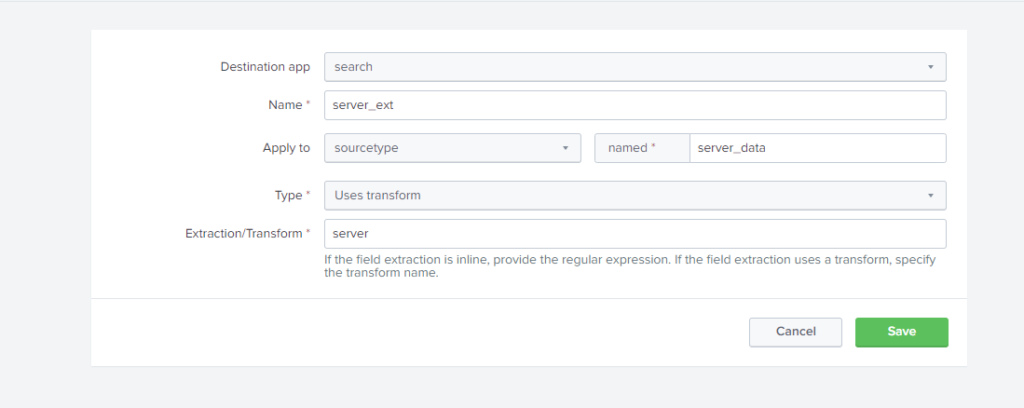
Do not forget to change the permission to Global in Field Transformation & Field Extraction as I mention at the last in Method 1.
Now, If we want to extract more fields from the same data, then follow same procedure from start as mention in Method 2, as shown below:

Then go to settings>field>fields extraction, and fill the information asked as shown below:
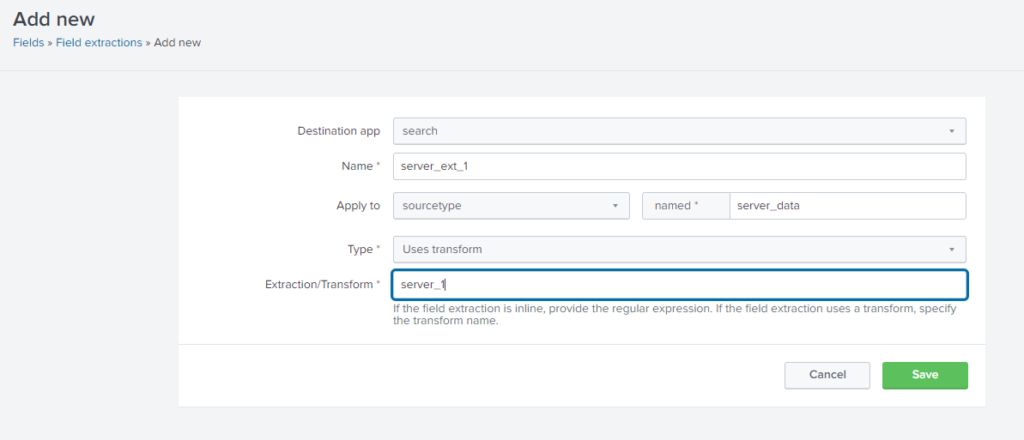
Now, let us see how our props.conf and transform.conf look in the backend.
props.conf
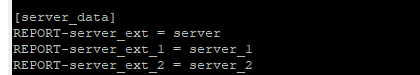
transforms.conf
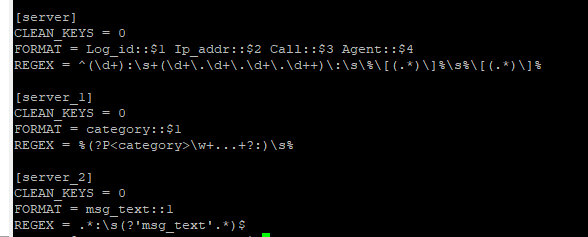
Notice the Different ways the REGEX is written in each stanza in transforms.conf
If you are still facing an issue regarding search time field extraction in splunk. Feel free to Ask Doubts in the Comment Section Below and Don’t Forget to Follow us on 👍 Social Networks. Happy Splunking 😉