Managing users and their access to Splunk collected logs is a very important aspect of access control to avoid unauthorized access to sensitive data/logs. You can add users to Splunk by using the following three methods. The most commonly used approach is configuring LDAP authentication or commonly called AD authentication.
As in any Enterprise Active Directory is used for user management.
We can use existing AD configuration to add and manage/update users in Splunk
Authentication methods supported by Splunk
- Splunk built-in authentication
- LDAP authentication (if enabled)
- Scripted authentication (if enabled)
Prerequisites for AD authentication
- Active Directory domain is set up.
- Created records in DNS for ldap.example.com.
- An Enterprise CA in our Active Directory and all our domain controllers have certificates.
Steps:
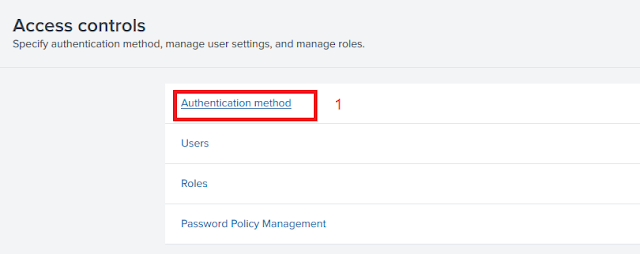
1. Logon to Splunk and then open the setting click on Access Control.
2. Click on the authentication method.
3. Click on LDAP and then click “Configure Splunk to use LDAP”.
4. Now you will get main LDAP strategy configuration settings page.
Following are the main AD items that you need to enter here.
- a. LDAP connection settings – based on connection settings Splunk will talk to AD.
LDAP strategy name: just a name.
You can have multiple LDAP strategies such as –
(i) strategy one for ready only access through an AD Group mapping to Splunk roles
(user & power user),
(ii) strategy two for full access through another AD Group mapping to other Splunk roles
(Admin, Splunk-system-role) or similar.
Default Splunk roles are – admin, can_delete, power, splunk-system-role, user.
Port number: 389 (this is AD LDAP default)
Connection order: default
Bind DN: cn= AcctName Splunk,ou=yourSvcAcctOU,dc=yourDCName,dc=yourDCExtension
This is the distinguished name of your Splunk account that you created in AD. It is recommended you should not use the default AD administrator account or your own AD login here. You should create a dedicated account for Splunk – no AD administrative privilege required on this account.
Bind DN Password: enter the password of the AD Splunk account
- b. User Settings – Splunk will look for users in AD based on this
User base DN: dc=yourDCName,dc=yourDCextension
- c. Group settings – Splunk will look for AD groups in AD based on this
Group base
DN:cn=Group_Splunk_Access_Admins,ou=youGroupOUName,dc=yourDCName,dc=DCextension
This is the AD group that been created to grant access in Splunk.
Static member attribute: member
- d. Dynamic group settings – optional.
- e. Advanced settings – default is ok; however you can increase search request size limit.
5. Click on the “Save”. If entered parameters are not correct – you won’t be able to save.
6. Now you should be able to see your LDAP strategy. Make sure it is enabled.
7. To see your AD group in Splunk, click on “Map groups”.
To map Splunk role(s) to an AD group – click on “Map groups > AD Group Name >
available and selected roles”;
Also, you should be able to see AD users at “Settings > Access controls >Users”. Make sure AD users are members of the Splunk group that been created on AD.
That’s all Your AD authentication is ready now and users from AD whose group mapped in Splunk can login to Splunk.
If you are still facing issue regarding configuring ldap authentication Feel free to Ask Doubts in the Comment Box Below and Don’t Forget to Follow us on 👍 Social Networks, happy Splunking >😉