How to Perform CIDR Lookup in Splunk
When working with network logs and IP addresses, you may often need to check if certain IPs belong to specific ranges, such as your organization’s office network. This is where CIDR (Classless Inter-Domain Routing) comes in handy. CIDR helps group IP addresses into ranges, allowing us to manage and work with large IP addresses more efficiently.
In this blog, we’ll walk through setting up and using CIDR lookups in Splunk to map IP addresses to their respective office locations based on predefined ranges.
What is CIDR?
CIDR (Classless Inter-Domain Routing) is a way to group IP addresses into ranges, which simplifies network management. For example, instead of listing each IP in a network like:
- 168.0.1
- 168.0.2
- 168.0.3
- …
- 168.0.255
We can use a CIDR notation, like 192.168.0.1/24, which represents the entire range from 192.168.0.1 to 192.168.0.255. This shorthand notation improves efficiency and is widely used in networking.
Problem: Identifying IPs Outside the Office Network
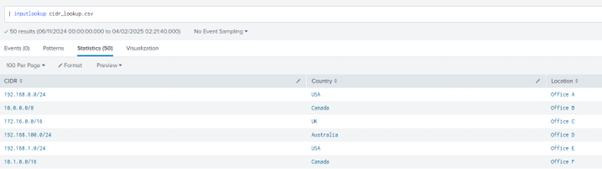
You have an index called _internal in Splunk, which contains logs for all the IPs your services are using. You also have a lookup file called cidr_lookup.csv, which maps office IP addresses to their corresponding subnet ranges in CIDR format, along with their locations.
Your goal is to determine the office location associated with each IP address in your logs. To achieve this, we will use a CIDR lookup to match IPs against predefined subnet ranges and retrieve their respective office locations.
Solution: Setting Up a CIDR Lookup in Splunk
To get started, we’ll use Splunk’s lookup command and create a CIDR lookup to filter IPs in your dataset.
Step 1: Upload the Lookup File
First, make sure your cidr_lookup.csv file (containing the office network ranges in CIDR format) is uploaded to Splunk.
Step 2: Configure the CIDR Lookup
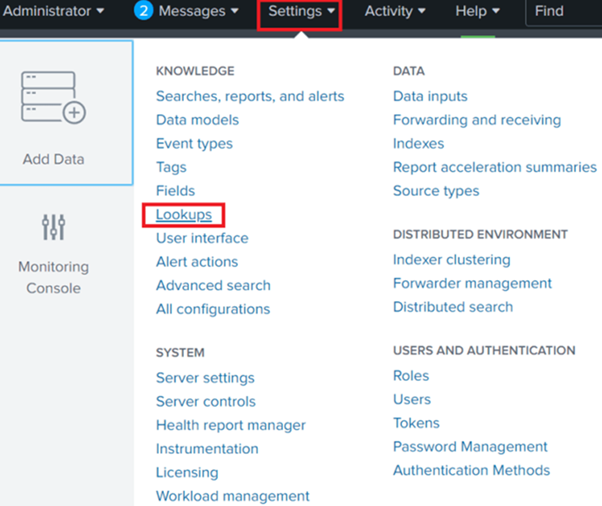
- Navigate to Settings > Lookups: This is where you will configure all your lookup definitions in Splunk.
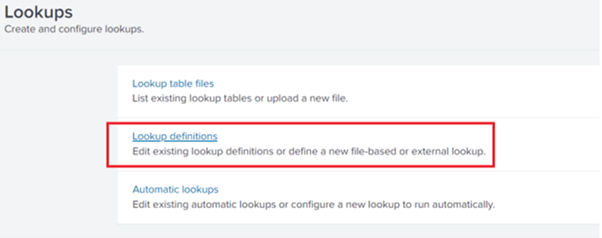
2. Create a New Lookup Definition: Click on Lookup Definitions and then click on New.
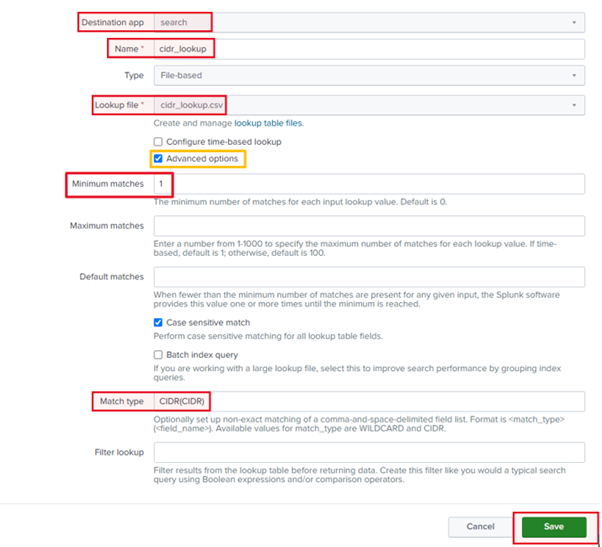
3. Set Up the Lookup Definition:
- Destination App: Choose the appropriate app (or leave it as the default).
- Name: Set a name for your CIDR lookup (e.g.,cidr_lookup).
- Type: Select File-Based.
- Lookup File: Choose the lookup file you uploaded earlier (e.g.,csv).
4. Configure Advanced Options:
- Minimum Matches: Set this to 1 to ensure at least one match is required for the lookup to return results.
- Match Type: Select CIDR and specify the field in your lookup file that contains the IP address or subnet (e.g., CIDR (CIDR )).
5. Save the Lookup Definition.
Step 3: Use the CIDR Lookup in a Search
Now that your CIDR lookup is defined, you can use it in your searches to identify the office location associated with each IP address.
For example, you can run a search like this:
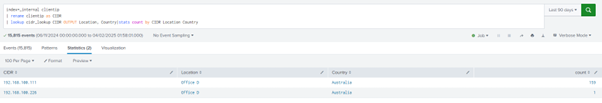
index=_internal clientip
| rename clientip as CIDR
| lookup cidr_lookup CIDR OUTPUT Location, Country|stats count by CIDR Location Country
Important Findings:
- We need to use the rename command before the lookup command to rename the clientip field (present in the _internal index) to CIDR. This is crucial because the lookup file matches IPs based on the CIDR Without renaming, the lookup won’t work as expected since clientip and CIDR are treated as different fields in Splunk. Ensuring the field names match allows Splunk to accurately map IP addresses to their corresponding Location and Country from the lookup file.
- We use the stats count by CIDR Location Country command to aggregate the results and avoid multiple events for the same IP. Without this, Splunk would return multiple entries for each occurrence of an IP in the logs, making it harder to analyze the data efficiently. The stats count function helps by grouping events based on CIDR, Location, and Country, providing a cleaner and more structured output that shows the number of occurrences for each unique IP-location pair.
Explanation:
- lookup: This command fetches data from the cidr_lookup. We match the IP field from the indexed data with the CIDR field from the lookup file.
- OUTPUT: The Location field from the lookup file is extracted, which indicates the office location associated with the IP address.
Conclusion:
Using a CIDR lookup in Splunk, you can efficiently map IP addresses to their respective office locations. This is especially useful for monitoring, security, and auditing, allowing you to track which office an IP belongs to and analyze network activity accordingly. With the CIDR lookup in place, managing large-scale IP data and gaining insights into office-specific network traffic becomes seamless.
If you are still facing an issue, feel free to Ask Doubts in the Comment Section Below and Don’t Forget to Follow us on 👍 Social Networks.
| Happy Splunking 😉