Prerequisites to creating and signing your own TLS certificates
Before you can create and sign your own certificates, you must have the following:
- Administrative access to the Splunk Enterprise instance on which you want to generate and sign the certificates.
- Access to a shell prompt, command line, or Terminal window. You can only create and sign certificates from the command line.
We have to go through these below steps to access TLS certificate
- Create the root certificate authority certificate
- Create server certificates and sign them with the root certificate authority certificate
- Create a single combined certificate file
- Configure Splunk Web to use TLS certificates
Create the root certificate authority certificate
The root certificate authority certificate serves as the base certificate that you use to sign the certificates that you’ll distribute to the Splunk platform instances in your deployment. It’s called the “root certificate authority certificate” for this reason: You, as the certificate authority, establish that you trust the certificates that are based on this root certificate.
You only need to create one root certificate authority certificate
- Open a command line interface, for example, a shell prompt, or a Terminal or PowerShell window.
- Create a new directory within the Splunk platform instance installation for the certificates.
mkdir $SPLUNK_HOME/etc/auth/mycerts
- Create a private key for your root certificate authority certificate.
$SPLUNK_HOME/bin/splunk cmd openssl genrsa -aes256 -out myCertAuthPrivateKey.key 2048
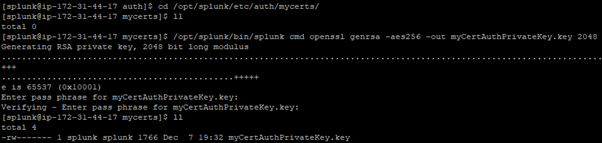
- When the OpenSSL program prompts you, enter a password for the key. The OpenSSL program then creates a file myCertAuthPrivateKey.key.
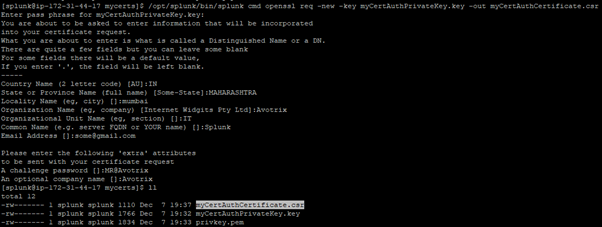
- Use the private key myCertAuthPrivateKey.key to generate a CSR for your certificate:
$SPLUNK_HOME/bin/splunk cmd openssl req -new -key myCertAuthPrivateKey.key -out myCertAuthCertificate.csr
- When the OpenSSL program prompts you, enter the password you created for your private key myCertAuthPrivateKey.key.
- The OpenSSL program asks for several different fields. At a minimum, provide values for the following:
- Country Name
- State or Province Name (full name)
- Locality Name (eg, city)
- Organization Name (eg, company)
- Organizational Unit Name (eg, section)
- Common Name (e.g. server FQDN or YOUR name)
- Email Address
- After you enter the information, the OpenSSL program creates a new CSR file called myCertAuthCertificate.csr
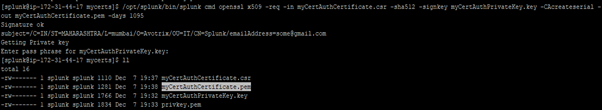
- Use the CSR file you created and sign it with the private key you created previously to create the root certificate authority certificate.
$SPLUNK_HOME/bin/splunk cmd openssl x509 -req -in myCertAuthCertificate.csr -sha512 -signkey myCertAuthPrivateKey.key -CAcreateserial -out myCertAuthCertificate.pem -days 1095
- When the OpenSSL program prompts you, enter the password you created for your private key myCertAuthPrivateKey.key again. The OpenSSL program creates the root certificate authority certificate file called myCertAuthCertificate.pem.
Create server certificates and sign them with the root certificate authority certificate
After you have created the root certificate authority certificate, you can create additional certificates and then sign them with your root CA certificate.
Similar to a root CA certificate, you have to create a private key and a certificate signing request to generate a certificate for a Splunk server.
- Create a private key for the server certificate.
$SPLUNK_HOME/bin/splunk cmd openssl genrsa -aes256 -out myServerPrivateKey.key 2048
When the OpenSSL program prompts you, enter a password for the key. The OpenSSL program then creates a file myServerPrivateKey.key
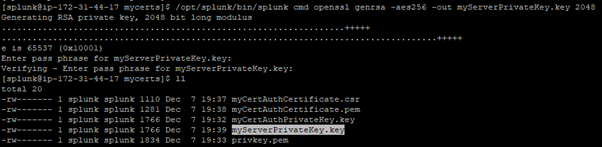
NOTE: Do not use the same password you used to sign the private key for the certificate authority certificate.
- Use the private key myServerPrivateKey.key to generate a CSR for your certificate:
$SPLUNK_HOME/bin/splunk cmd openssl req -new -key myServerPrivateKey.key -out myServerCertificate.csr
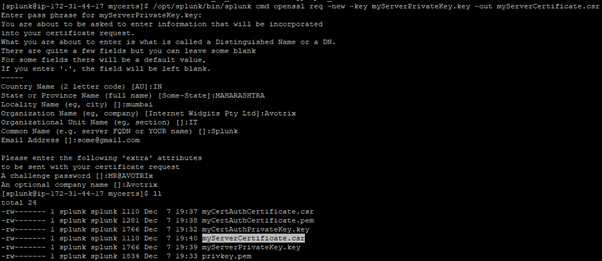
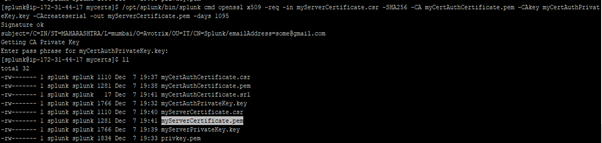
- Use the CSR file you created and sign it with the private key you created previously, the certificate authority certificate, and its private key to create the server certificate.
- When the OpenSSL program prompts you, enter the password you created for the private key myCertAuthPrivateKey.key again. The OpenSSL program creates the server certificate file called myServerCertificate.pem.
$SPLUNK_HOME/bin/splunk cmd openssl x509 -req -in myServerCertificate.csr -SHA256 -CA myCertAuthCertificate.pem -CAkey myCertAuthPrivateKey.key -CAcreateserial -out myServerCertificate.pem -days 1095
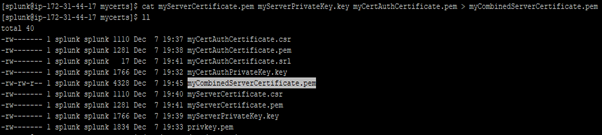
Create a single combined certificate file
TLS certificates let you secure communication between Splunk Enterprise components from end to end. After you get the certificates.you must combine the server certificate, the private key, and the public certificate, in that order, into a single file. The combined file must be in privacy-enhanced mail (PEM) format.
cat myServerCertificate.pem myServerPrivateKey.key myCertAuthCertificate.pem > myCombinedServerCertificate.pem
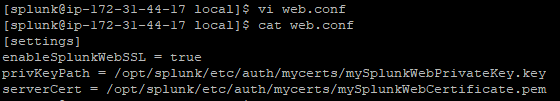
Configure Splunk Web to use TLS certificates
- Open or create a local web.conf configuration file for the Search app in $SPLUNK_HOME/etc/system/local
- Under the [settings] stanza, configure the path to the file that contains the web server SSL certificate private key file and the path to the Splunk web server certificate file.
[settings]
enableSplunkWebSSL = true
privKeyPath =/opt/splunk/etc/auth/mycerts/mySplunkWebPrivateKey.key
serverCert =/opt/splunk/etc/auth/mycerts/mySplunkWebCertificate.pem
- save the file and close it.
- Restart the Splunk Enterprise instance:
# $SPLUNK_HOME/bin/splunk restart splunkd
If you are still facing an issue, feel free to Ask Doubts in the Comment Section Below and Don’t Forget to Follow us on 👍 Social Networks. Happy Splunking 😉






