Secure Sockets Layer (SSL) certificates that come from third parties are the most secure way to protect communications between your Splunk platform infrastructure from potential security breaches. In this context, “inter-Splunk communication” means any type of communication that does not involve Splunk Web.
Steps to obtain a third-party certificate for inter-Splunk communication
Create a certificate signing request to send to a CA
If you want, you can create and sign a CSR to send to a CA to acquire a third-party certificate. The CSR is based on the private key and certificate signing request file that you create in the procedures that follow. The CA takes the CSR, generates your certificate, and signs it. Some CAs do not charge for this, but might limit the kinds of certificates they issue for free.
In general, submitting a CSR involves visiting the certificate authority website, filling out a form, possibly paying a fee, then sending or uploading the CSR file. Because each CA has their own process for accepting this information, there is no specific process for providing the necessary information to get a TLS certificate.
All of the certificates that you download must be in privacy-enhanced mail (PEM) format. If your certificate authority does not provide you with certificates in this format, you can convert them to PEM format using the OpenSSL binary that comes with the Splunk platform installation. The program must be able to read the existing file format and write to PEM format. Consult the OpenSSL documentation for more information about converting certificate file formats.
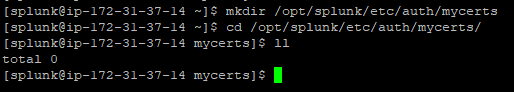
- Connect to the Splunk platform instance where you want to generate the CSR. Create a new directory within the Splunk platform instance installation for the certificates.
mkdir $SPLUNK_HOME/etc/auth/mycerts
- Create a private key for your certificates The following example uses Advanced Encryption Standard (AES) encryption and a 2048-bit key length.
$SPLUNK_HOME/bin/splunk cmd openssl genrsa -aes256 -out myServerPrivateKey.key 2048
When the OpenSSL command prompts for a password, type in one. The OpenSSL command then creates a file myServerPrivateKey.key.
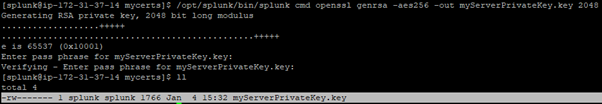
- Use the private key keyto generate a CSR for your certificate: When prompted, type in the password you created for your private key myServerPrivateKey.key.
$SPLUNK_HOME/bin/splunk cmd openssl req -new -key myServerPrivateKey.key -out myServerCertificate.csr

Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
Configure Splunk Web to use TLS certificates
Open or create a local server.conf configuration file for the Search app in $SPLUNK_HOME/etc/system/local. If you use a deployment server, you can create this file in any application directory that you make available to the deployment server for download to deployment clients.
Under the [settings] stanza, configure the path to the file that contains the web server SSL certificate private key file and the path to the Splunk web server certificate file.
The following example shows an edited settings stanza:
[settings]
enableSplunkWebSSL = true
privKeyPath = /opt/splunk/etc/auth/mycerts/mySplunkWebPrivateKey.key
serverCert = /opt/splunk/etc/auth/mycerts/mySplunkWebCertificate.pem
Save the file and close it.

Restart the Splunk Enterprise instance.
If you are still facing an issue, feel free to Ask Doubts in the Comment Section Below and Don’t Forget to Follow us on 👍 Social Networks. Happy Splunking 😉